Cybersecurity has evolved dramatically over the past decade. Once confined to IT silos, cybersecurity has evolved into a vital pillar of organizational success. Yet despite this evolution, a significant gap still exists between cybersecurity strategy and business strategy, and this disconnect creates serious vulnerabilities for organizations.
According to PwC's Global Digital Trust Insights 2024 report, only 27% of business leaders strongly agree that their cybersecurity strategy is well aligned with their overall business strategy, despite 74% naming cybersecurity as a top priority. This misalignment isn't just a technical problem; it creates threats to decision-making, innovation, customer trust, and ultimately, business growth.
In today's threat landscape, security breaches impact everything from customer data and confidence to market performance and reputation. That's why aligning cybersecurity with business goals is no longer optional; it's a strategic necessity for long-term resilience and growth.
Modern organizations face an ever-expanding attack surface as digital transformation accelerates. Cyber-attacks are not only more frequent but increasingly sophisticated, targeting intellectual property, revenue-generating systems, operational infrastructure, and reputation. When cybersecurity strategy is embedded into business strategy, it shifts from being viewed as a cost center to becoming a competitive advantage.
Cybersecurity is now an important part of the whole business plan, not just an IT concern. It protects critical data, systems, and customer information from unauthorized access and cyber threats. More importantly, a strong security posture builds trust with customers and business partners, which is essential for growth and market expansion.
Organizations that treat cybersecurity as a business enabler can:
Despite the clear need for alignment, many organizations struggle with a fundamental disconnect between security teams and business leadership. Understanding these gaps is the first step toward bridging them.
These disconnects lead to friction, poor prioritization, and underutilized resources. More seriously, they leave organizations vulnerable to threats that could have been prevented with better alignment.
Successfully aligning cybersecurity with business strategy requires adopting several fundamental principles:
Frame cybersecurity conversations around the risks that matter most to business operations: operational downtime, critical data loss, reputational damage, and non-compliance with regulatory frameworks. By identifying risks with the most significant financial and operational impact, security teams can prioritize more effectively and demonstrate how security protects business continuity.
Focus on protecting what matters most to your operations. Not all systems or data are equally critical. Use a risk-based approach to focus security investments on areas that support innovation, customer trust, and operational continuity. For example, securing customer-facing applications or sensitive financial platforms typically takes precedence over lower-impact assets.
To effectively integrate cybersecurity into business planning, organizations must perform ongoing audits and risk assessments. These processes help identify new vulnerabilities, track the effectiveness of existing controls, and ensure that risk mitigation efforts evolve alongside the threat landscape and business operations.
Move beyond periodic compliance checklists. Frequent risk assessments, threat modeling, and regular penetration testing help identify vulnerabilities early, allowing for proactive mitigation and informed security investments.
Involving board members, C-suite executives, and top management from the outset fosters a proactive approach to cybersecurity. By translating technical risks into language that aligns with strategic priorities, such as revenue growth, market expansion, or digital transformation, organizations enhance executive buy-in.
Regular engagement with executive leadership and business unit heads is essential. This allows security leaders to anticipate upcoming projects, understand emerging risks, and proactively design controls that support rather than hinder business objectives. When security and management communicate effectively, policies become stronger and more practical.
Establish meaningful key performance indicators (KPIs) that both technical and business stakeholders can align around. Move beyond technical metrics like patch counts or blocked attacks. Instead, track and report on metrics that resonate with executives:
Clear metrics enable accountability and continuous improvement while demonstrating the tangible value of cybersecurity investments.
View cybersecurity not as an expense but as critical protection that safeguards brand equity, strengthens customer relationships, and builds long-term trust. Shift the budget conversation from cost to value by prioritizing investments based on potential impact to innovation, customer trust, and operational continuity—not just regulatory requirements.
❌ “We need USD2M for a new firewall.”
✅ “This USD2M investment prevents a USD25M breach in our payment platform.”
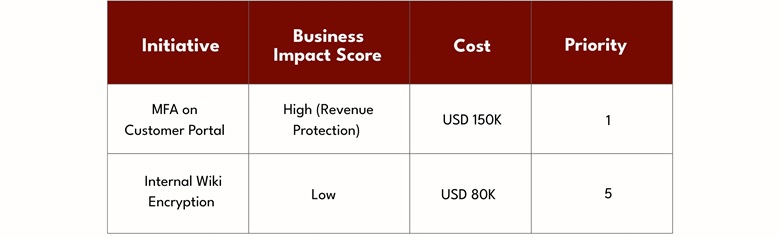
Use a Business Value Matrix to rank initiatives:
Here are proven best practices:
Ensure cybersecurity is part of every major business decision, from product development and market expansion to mergers and acquisitions. Involve security teams in the earliest stages of product development, cloud migrations, and third-party integrations. This "shift left" approach reduces costly rework and ensures new technologies are secure by design.
Each organization must assess its vulnerabilities based on its data, technology stack, and role in the supply chain to build a strategy that reflects real-world risk exposure.
Implement layered security that includes multi-factor authentication, firewalls, secure configurations, and access controls. Multi-factor authentication is essential for protecting critical assets like customer data, while encryption and malware prevention technologies safeguard sensitive information from evolving cyber threats.
Prepare for disruption with a structured incident response plan that outlines roles, escalation paths, and recovery procedures. This ensures rapid action during a breach and supports ongoing business continuity efforts. Conduct regular tabletop exercises to simulate ransomware attacks, supply chain breaches, or regulatory incidents to test and refine response plans.
Security is no longer just the IT department's job. Launch ongoing awareness programs, phishing simulations, and role-based training to empower employees to recognize and report threats at every level. Train employees regularly on how to recognize cyber threats, use strong passwords, and prevent phishing attacks.
Embed cybersecurity into daily operations through collaboration, shared responsibility, and continuous employee training. A strong security culture ensures that strategies are not only defined but consistently practiced by every employee, team, and department. A security-aware workforce is a powerful defense.
Translate technical risks into business-relevant language for C-suite and board members. Use the shared KPIs discussed earlier to track progress and support informed decision-making. Regular reporting on security posture, emerging threats, and risk mitigation efforts keeps leadership engaged and informed.
Replace jargon with impact:

Invest in advanced technologies such as AI-driven threat detection, automated incident response, and security software that can scale alongside business growth. These tools analyze vast amounts of data in real time, identify subtle anomalies, and respond to threats faster.
Sometimes expert help is needed to test and improve defenses. Working with penetration testing services and cybersecurity professionals ensures you're covering all bases and identifying gaps before attackers do.
While aligning cybersecurity with business goals is essential, the path forward isn't always clear, especially for organizations without dedicated in-house security leadership. In these cases, partnering with external experts can be practical and high impact.
A virtual Chief Information Security Officer (vCISO) offers strategic guidance, risk management, and board-level communication needed to close the gap between cybersecurity strategy and business objectives. This flexible model allows organizations to elevate their cybersecurity posture without the cost or complexity of hiring a full-time CISO.
Organizations often turn to vCISO services when they're preparing compliance with regulations, need risk-based decision-making at the leadership level, or require support aligning security controls with long-term business goals.
If you're unsure whether your cybersecurity measures truly support your business goals, look for these warning signs:
If any of these feel familiar, it may be time to reframe your security function as a strategic business enabler.
True business resilience requires more than reactive security measures. It demands leadership alignment, strategic prioritization, and the ability to adapt to an ever-changing cyber threat landscape.
By positioning cybersecurity as a catalyst for innovation and growth rather than a cost center, organizations can thrive in an increasingly digital, interconnected, and risky world. When security and business strategy move forward together, guided by visionary leadership and a shared commitment to resilience, cybersecurity transforms from a technical necessity into a true competitive advantage.

CredBadge™ is a proprietary, secure, digital badging platform that provides for seamless authentication and verification of credentials across digital media worldwide.
CredBadge™ powered credentials ensure that professionals can showcase and verify their qualifications and credentials across all digital platforms, and at any time, across the planet.

Keep yourself informed on the latest updates and information about business strategy by subscribing to our newsletter.